Sadly, the support for passkeys is still lacking.
I still have no idea how passkeys work. All the explanations I’ve seen so far were less than helpful.
As I understand it, instead of the website or online service storing your password (in a, supposedly secured way), with passkey your password manager stores a private key and the online service stores a public key (or rather a lock). The key and the lock are paired together cryptographically (mathematical functions that are non-reversible). Now when you login with passkey, the service sends a challenge generated from the lock, that can be solved only with the matching private key, your password manager solves the challenge and your authenticated. Locks and keys were not exchanged during the process, and services never store your key. Everything happens automagically.
It actually uses the same protocol used is some hardware security keys such as Yubikey and Solokeys. The problem remains the same as with hardware security keys, adoption and support, compatibility. It’s very rare that a service supports these options, although they exist for a while.
Anyone feels free to correct me if I wrote something wrong. I am by no mean an expert.
Is there any way to use passkeys without anything Google or Apple or smartphone?
Bitwarden has clients for Windows and Linux, and extensions for Firefox, Chrome. You can use passkeys this way. I self-host Bitwarden (vaultwarden) and this is how I use passkeys, via Android app and Firefox extension on Linux. IDK if the flatpakinux client would allow you to use passkeys.
Hm, I do host myself a vaultwarden-web instance and I don’t see an option for passkeys. Time to update I guess, although it’s not that old - 2024.1.2
Passkey will show once you have registered one for a given website. Usually, when registering for a website that offers passkey login, it will offer you to register a passkey when creating your account, then you can unlock your vault from the bitwarden extension and register the passkey. Otherwise for an already existing account, you can go to your account/security settings for this website, if they offer passkey login, it will be in the same section as for security keys (yubikey, solokeys), the registration process is similar to registering a hardware security key, only bitwarden will act as the passkey. You can see it as a de-materialized security key.
Your explanation is correct.
For me, the critical issue is still compatibility. Not all password managers support passkeys, not many sites support passkeys etc.
Imagine SSH Key but for Website
Dear google, can I have custom passkey provider on my Android <13?
Google:
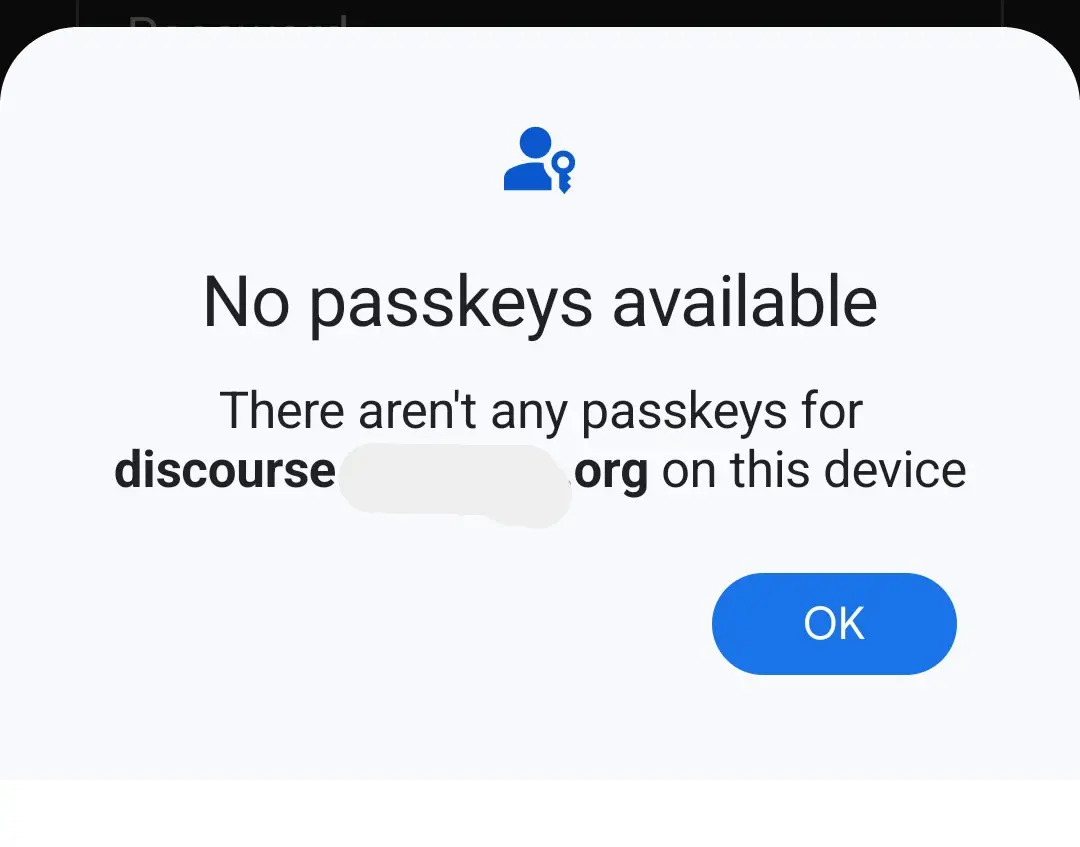
Spoiler: There’s no option to change the passkey provider nor even mention of passkeys in settings
While annoying it’s understandable that they don’t backport everything from newer updates.
What about SQRL?
If you can remember all your passphrases, is randomly generated enough of a benefit to justify having a centralized vulnerability?
I couldn’t possibly remember all my passphrases unless I reused them everywhere, which would leave me with an arbitrary number of centralized vulnerabilities, under the responsibility of people who don’t give a shit.



